hash tree
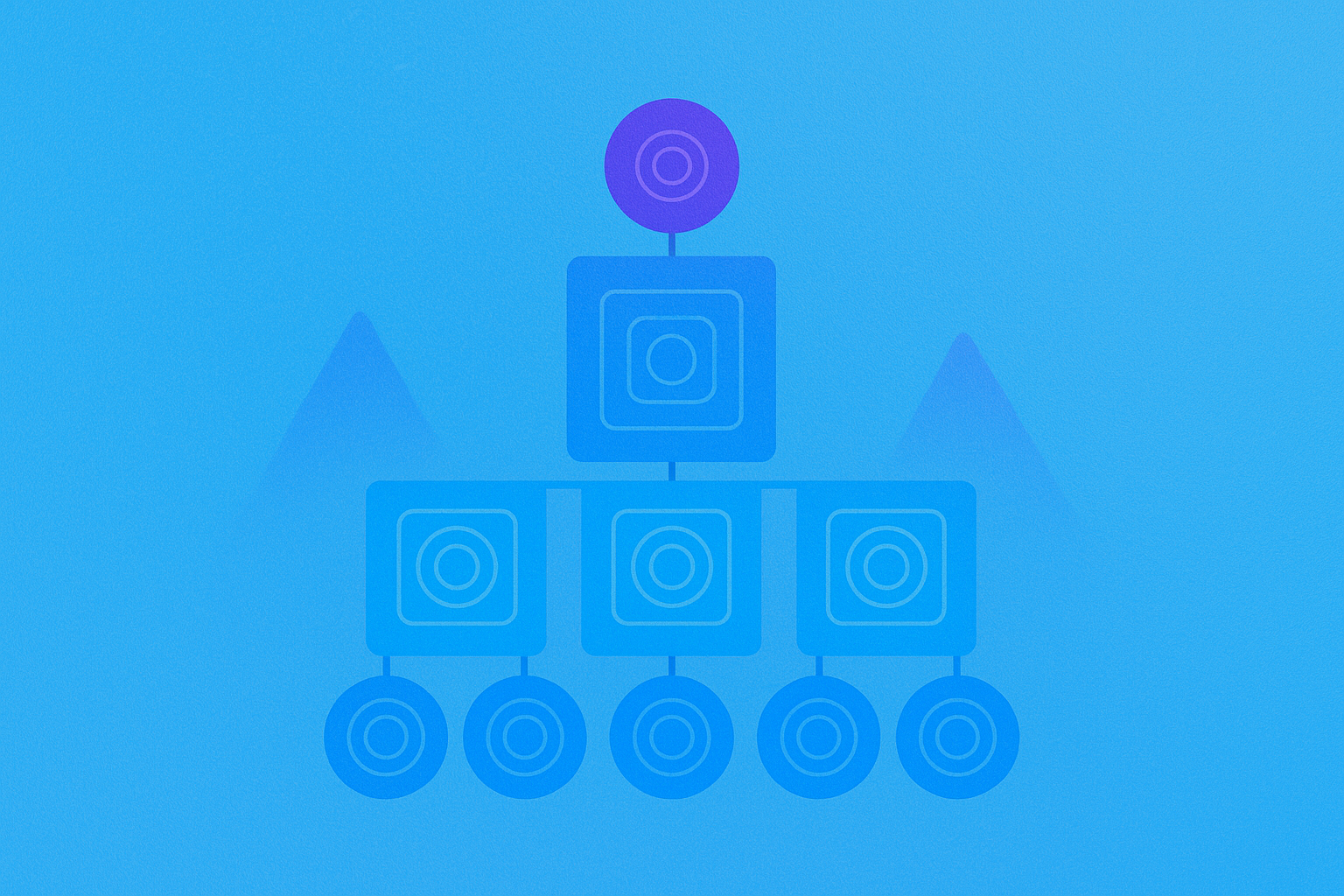
Hash trees (also known as Merkle trees) are tree-like data structures built using cryptographic hash functions that efficiently verify the integrity of large datasets through hierarchical verification. In a hash tree, leaf nodes contain hash values of original data blocks, while non-leaf nodes contain combined hashes of their child nodes. This structure ensures that even tiny changes to any data will cause significant changes to the root hash (Merkle root), providing an efficient and secure mechanism for data verification, auditing, and synchronization. Hash trees play a crucial role in blockchain technology, allowing lightweight clients (SPV clients) to verify transaction validity without downloading the entire blockchain, and serving as the foundational technology for ensuring data consistency across Bitcoin, Ethereum, and many other blockchain networks.
Background: Origin of Hash Trees
Hash trees were originally proposed by Ralph Merkle in 1979, hence the alternative name Merkle trees. They were initially designed for efficient handling of digital signatures, allowing one signature to verify multiple messages. Over time, the application range of hash trees gradually expanded.
Before the emergence of cryptocurrencies, hash trees were widely used in distributed systems, version control systems, and file systems (such as Git and IPFS) for efficiently detecting data differences and synchronization.
In 2008, Satoshi Nakamoto introduced the Merkle tree structure in the Bitcoin whitepaper, establishing it as a core component of the Bitcoin blockchain for efficient transaction verification. This laid the foundation for hash trees in blockchain technology, and subsequently, almost all mainstream blockchain projects adopted some form of hash tree structure.
The design of hash trees addresses a key challenge in distributed systems: how to verify the existence and integrity of specific data without transmitting the entire dataset. This feature is particularly important for lightweight clients in blockchain, enabling them to run on resource-constrained devices.
Work Mechanism: How Hash Trees Function
The construction and verification process of hash trees follows these core steps:
- Data partitioning: Dividing original data into fixed-size blocks.
- Leaf node generation: Applying a hash function (such as SHA-256) to each data block to generate leaf node hash values.
- Internal node construction: Pairing and combining adjacent nodes' hash values, applying the hash function again to generate upper-level nodes until reaching the root hash (Merkle root).
- Verification path (Merkle path): To verify a specific data block, only the sibling node hash values along the path from that data block to the root node need to be provided.
Hash trees come in several variants to suit different application scenarios:
- Binary hash trees: The most common form, where each non-leaf node has two child nodes.
- Multi-way hash trees: Each non-leaf node can have multiple child nodes, improving branching efficiency.
- Sparse Merkle trees: Only storing leaf nodes with non-zero values, optimizing storage space.
- Merkle Patricia Trees (MPT): A special structure used by Ethereum that combines features of Merkle trees and prefix trees.
In blockchains, hash trees are typically used for:
- Transaction verification: Lightweight clients can verify transactions without downloading entire blocks.
- State synchronization: Efficiently synchronizing blockchain state by transmitting only necessary data.
- Privacy protection: In zero-knowledge proofs, proving knowledge of certain data without revealing its content.
What are the risks and challenges of Hash Trees?
Despite providing efficient data verification mechanisms, hash trees face several challenges and limitations in practical applications:
- Computational overhead: For frequently updated large datasets, recalculating the hash tree can impose significant computational burden.
- Hash collision risk: Though extremely unlikely, there's a theoretical possibility of hash collisions that could lead to verification failures or security vulnerabilities.
- Merkle path overhead: In some application scenarios, verification paths may become very long, increasing data transmission and storage costs.
- Implementation complexity: Maintaining hash tree consistency can become complex, especially when handling dynamic datasets.
- Second preimage attack: In some implementations, if the hash function is poorly chosen or implemented with flaws, there may be risks of second preimage attacks.
To address these challenges, blockchain projects typically adopt:
- Optimized tree structure designs, such as Ethereum's MPT (Merkle Patricia Tree).
- Incremental update mechanisms to avoid completely rebuilding the tree structure.
- Secure hash algorithm selection and implementation specifications.
- Regular auditing and security assessments of hash tree implementations.
Hash trees are fundamental technical components in cryptocurrencies and blockchain systems, and developers need to deeply understand their advantages and limitations to make appropriate design choices for specific application scenarios.
Hash trees represent a perfect fusion of data structures and cryptography in blockchain technology, providing an efficient and secure method for data verification in decentralized systems. As a key technology for blockchain scalability and lightweight client implementation, hash trees make it possible to verify large numbers of transactions in resource-constrained environments while maintaining low storage and bandwidth requirements. As blockchain technology continues to evolve, the applications of hash trees are continuously expanding, from basic transaction verification to zero-knowledge proofs, state channels, and sharding technology, demonstrating their wide applicability as cryptographic tools. Despite facing some technical challenges, the fundamental principles of hash trees have been widely validated and will continue to exist as core infrastructure for blockchains and distributed systems.
Related Articles

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Solana Need L2s And Appchains?
