- Topic1/3
14k Popularity
33k Popularity
17k Popularity
6k Popularity
174k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is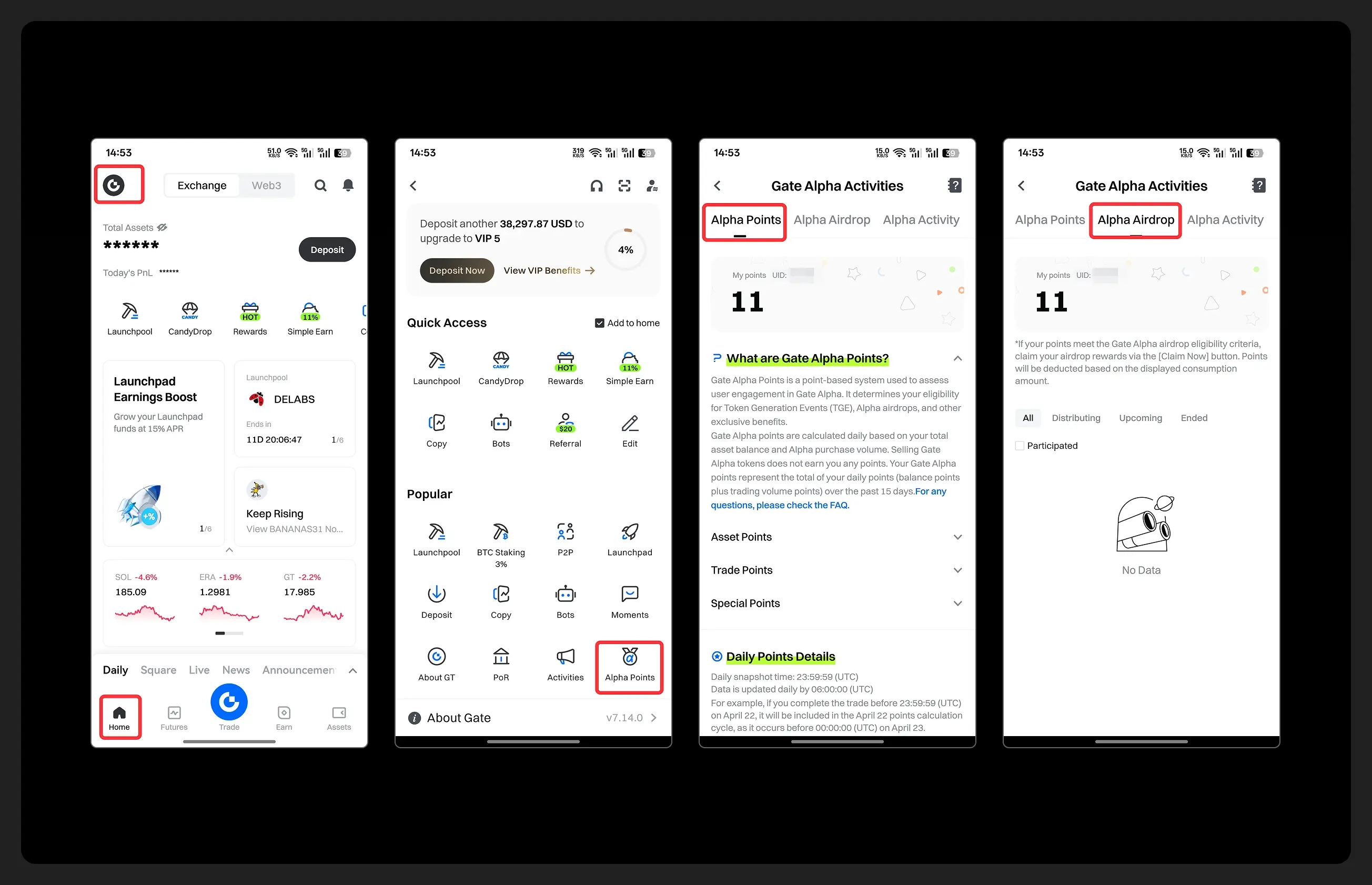
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Integration of Web3.0 and Web2.0: New Challenges and Opportunities in Cybersecurity
The Integration of Web2.0 and Web3.0: New Challenges in Cybersecurity
Driven by the wave of digitalization, the integration of Web2.0 and Web3.0 has become an inevitable trend. This integration not only brings new opportunities but also presents unprecedented security challenges.
The emergence of Web3.0 is seen as a hope for building a more secure and transparent internet. It aims to address the long-standing issues of privacy and data control inherent in centralized Web2.0 systems. However, as Web3.0 develops, it often interacts with the Web2.0 network in dangerous ways, and this intertwining of risks provides fertile ground for new types of cybersecurity threats. If these potential issues are not controlled, they may undermine the security that Web3.0 offers.
Although many tech enthusiasts actively embrace Web3.0, the transition from Web2.0 to Web3.0 is not smooth sailing. During this process, newly emerged security vulnerabilities can easily be exploited by hackers and phishers. Therefore, in order to build a more secure digital ecosystem, Web3.0 must first pay attention to and address the weaknesses left over from Web2.0.
Key Vulnerabilities at the Intersection of Web2.0 and Web3.0
Web2.0 and Web3.0 represent two completely different ways of processing internet data. Web2.0 relies on centralized servers and data collection models, concentrating power in the hands of a few large companies. In contrast, Web3.0 uses blockchain's distributed ledger technology to return data ownership to users, thereby achieving decentralization of control.
However, these two systems are not completely independent; many Web3.0 applications still rely on the infrastructure of Web2.0, such as domain names, storage, and APIs. This dependency means that Web3.0 also inherits the centralization flaws of Web2.0. For example, Web3.0 platforms that use cloud service providers for off-chain storage may also be vulnerable to server exploit attacks. Similarly, those Web3.0 platforms with Web2.0 interfaces are also at risk of phishing attacks and DNS hijacking.
Phishing Attacks: Web2.0 Vulnerabilities in a Web3.0 Environment
Phishing attacks have long been a threat in the Web2.0 environment. In Web3.0, the methods of attack are basically similar: attackers imitate the interfaces of legitimate platforms to deceive users into revealing private keys or signing malicious transactions.
These attacks exploit the vulnerabilities of Web2.0, using tactics such as spoofing domain names and email scams to trick users into believing they are interacting with legitimate decentralized platforms. For example, phishing attacks targeting DeFi platforms may use counterfeit Web2.0 websites to deceive users and subsequently steal funds from their Web3.0 wallets. Therefore, the integration of Web2.0 and Web3.0 provides criminals with the opportunity to combine traditional phishing attacks with new technologies, posing a serious threat to users who mistakenly believe that decentralization itself can provide comprehensive protection.
The Transparency and Security Advantages of Web3.0's Decentralization
Despite the aforementioned risks, Web3.0 still brings hope for a safer internet through its decentralized technology and transparent framework. The blockchain, which is a pillar of Web3.0, is an immutable ledger that far surpasses the tamper resistance of traditional Web2.0 databases. At the same time, smart contracts eliminate the need for potentially vulnerable third parties, while decentralized identity solutions allow users to control their digital identities, effectively reducing the risk of phishing attacks.
In addition, the transparency of Web3.0 allows users to verify transactions and audit systems in real time, providing a level of security and accountability that is difficult to achieve in the opaque structure of Web2.0. By decentralizing control to multiple nodes, Web3.0 reduces the risk of large-scale data breaches common in centralized systems.
Accelerate the Web3.0 application process and reduce network security risks
To reduce the new security risks arising from the overlap between Web2.0 and Web3.0, it is essential to accelerate the adoption of comprehensive decentralized systems. As long as Web3.0 still partially relies on Web2.0 infrastructure, it will continue to be subjected to hybrid attacks that exploit the vulnerabilities of both systems.
The advantages of decentralized systems in enhancing security are evident. For example, in the DeFi space, users can trade directly without relying on third-party platforms, thereby reducing the risk of third-party vulnerability attacks. Additionally, decentralized applications (Dapps) built on blockchain networks allow users to interact with the platform securely without needing to log in or avoid centralized data storage.
However, to realize the full potential of Web3.0, developers and industry leaders must be committed to building decentralized infrastructure that operates independently of Web2.0. This means investing and incubating in relevant areas such as decentralized storage solutions, identity protocols, governance systems, and more. All these efforts aim to mitigate the inherent risks associated with the current reliance on Web2.0, in order to create a safer digital environment.